Did you know that one small business is successfully hacked every 19 seconds? In just seconds your business could be under attack and at the mercy of an online criminal. The repercussions of a chance attack can be far-reaching and devastating. While the implications of data theft or the cost of downtime and recovery are costing businesses on average over £4000 a time, the true financial impact of a cyber-attack is largely under-reported due to the sheer scale of damage incurred.
It is reported that 33% of UK organisations say they lost customers after a breach. Even after recovering from the loss of data and money, the operational time wasted and the often irreparably damaged reputation of your business; you could be facing the loss of some of your valuable customers. The trust is gone between you and your customers, and future leads may consider you a risky choice with a questionable lack of security. The irreversible impact on businesses can be catastrophic. And with a shocking 88% of businesses in the UK falling victim to a breach in the last year, this problem isn’t set to go away. As business owners, we need to address this for the benefit of our team’s livelihoods, the protection of our customers, and the future of businesses. In this discussion, we aim to give you an insight into the pitfalls that hundreds of businesses face and raise awareness of the important steps you can take to increase the security of your business. Take it from the experts, it’s worth listening in.
The very real risk to businesses
You may be thinking ‘this wouldn’t happen to me’ as we so often tend to when faced with the horrors of what could be and the worst-case scenarios. Unfortunately, any and every business can have a target on their back and no business is off-limits to scam artists and career hackers. Most often, the users are the weakest link in a system and make for the easiest entry point to gain access to details. The risk is not isolated to big corporations with huge pots of money to play with, nor is it simply smaller businesses who arguably cannot afford the sophisticated security levels others may be able to.
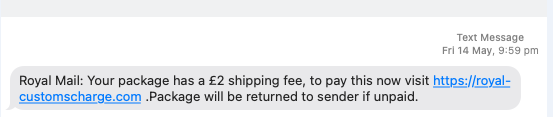
We are seeing a steady rise in businesses suffering from cyber-attacks, especially since the beginning of the pandemic. A particularly common example that we are seeing in recent times are SMS messages posing as Royal Mail and other postal services that encourage victims to input their details to receive a missed parcel. Concerning evidence shows businesses that have experienced a cyber breach are often targeted again as seemingly easy pickings. We can agree that this very real risk is something we need to educate ourselves on and learn how to combat but first we must learn about what exactly we are up against. So, what are the most common attacks that are affecting UK businesses?
Types of Cyber Attacks you need to know about
Phishing
One of the most common attacks to take place is phishing. Phishing refers to fraudulent emails being sent out that pose as trustworthy sources, they ultimately trick you into sharing personal information such as bank details. Phishing scams relating to the Coronavirus have led to over £800,000 being lost in the UK in 2020 alone. Globally, the financial figure rockets to around £400 billion. Many of our customers have experienced, and unfortunately, some have fallen foul, to these types of scam emails or texts. Often, scammers will adopt the persona of your boss and request that you transfer funds or purchase an Amazon gift card for a client. More recently, one of our clients received a fraudulent Dropbox link and was almost compromised, this was the second time they had experienced phishing in the same month.
The emails often look the part and can catch you off guard if you do not remain vigilant and wary. Treating every email with caution and suspicion is more critical than ever. Aaron, Glo DeskHelp Manager, shares his advice: ‘double-check the sender’s email address, look out for a lack of email signature and if personal details or payment is being requested, take the time to confirm with the purported person on another form of communication’. Despite the prolific nature of phishing, 22% of UK organisations do not host training for their staff to teach them about cybersecurity and best practice. Don't be a part of the statistic.
Battling BEC Scams
Another example of email fraud is Business Email Compromise (BEC) scams. These have proven particularly profitable for the criminal when you consider the substantial amounts of money typically paid via supplier invoices. Supplier invoicing scams are schemes that send victims fraudulent invoices that they pay or involve rerouting payment to a bank account controlled by the criminal.
These invoicing scams are scarily convincing and make for a costly mistake. While any size of business is a pretty target for scammers, huge companies like Toyota have hit the news as unfortunate scamming victims in recent years. Toyota Boshoku Corporation, a European sector of the company, felt the sting to the tune of close to $37 million. In the UK, email scams of this kind have risen over 58% in the last year and it continues to grow.
The Rise of Ransomware
Ransomware is carried out by gaining access to your systems and using malware to lock all your files and data from you. Criminals then approach demanding a ransom to release the locked files. A seriously debilitating attack: ransomware can rapidly grind a business to a halt and yield all power and resources.
You may recall the controversial ransomware attack launched on the UK’s National Health Service. Over 200,000 computers in over 150 countries were impacted as part of the attack, resulting in thousands of cancelled appointments and operations and rushed relocation of emergency patients. The NHS was brought to a near standstill as staff resorted to pen and paper and their personal mobiles to maintain data records during that time.
With organisations across the globe so heavily dependent on digital data records, automated systems, and software to continue operations, the fear of ransomware is very real. 48% of UK organisations were affected by ransomware in the last year, with 13% of organisations reportedly paying the ransom demanded of them. Remediation costs run into six-figure sums and with 32% of UK companies’ cybersecurity insurance not covering ransomware, businesses can be left in a precarious position.
No System is Safe
New and rampant cyber attacks are becoming ever prevalent, with specific systems and software targeted. Intelligent hackers seek new ways to delve into business’ accounts and data and gain access to large quantities of confidential and valuable information.
HAFNIUM: Microsoft Exchange Server breaches 2021
Take the series of HAFNIUM data breaches in the Microsoft Exchange Server as a prime example. Following 4 zero-day exploits that were discovered in on-site Microsoft Exchange Servers, there was a global wave of cyberattacks and data breaches that spanned across January 2021. Attackers were able to access user emails and passwords on compromised servers, take advantage of administrator privileges and tap into connected devices on the same network. Once hackers are in, they often install a backdoor that means they can maintain full access to the servers even when the impacted servers have been updated and seemingly restored to be secure.
As soon as the Glo team learned of this attack we alerted all our supported customers and arranged for servers to be updated and checked over. Unfortunately, one business that didn’t have our IT support had already been pwned and their server exploited. Luckily their issue was able to be resolved. While these events can occur often and seem a constant threat, we've included some steps later in this article to help you stay safe and secure.
Ubiquiti Breach
Another notable example of cyberattacks is the Ubiquiti breach that occurred impacting their customer’s devices and personal details. Businesses that opted for cloud-enabled Internet of Things (IoT) devices, such as routers and access points found that their account credentials shared with Ubiquiti had been exposed. This was due to a third-party cloud provider hosting customer information which evidently had not upheld the security measures that were required.
The breach was massive as it allowed access to customer data, as well as putting the devices of Ubiquiti customers deployed in businesses and homes around the world at risk.
Interestingly, it's been largely shared that the reports that were released downplayed the crisis, and information around it was legally silenced. The backlash of this secrecy and lack of transparency could stand as a valuable lesson to future businesses in a similar unfortunate circumstance.
Lastly, the Ubiquiti breach hammers home the importance of the decision you make around hosting for your business. Every business has different needs and therefore requires varying hosting options that fit the bill. We took the decision many years ago to host our own controller, which meant we were thankfully not hacked or impacted by this attack. Our customers, who otherwise could have been affected, were also protected from this due to our decision.
We’ve delved into the world of cyberattacks and shared examples of the kinds of risks that businesses are up against but what can you do to protect your business’ IT safety and wellbeing?
Important Steps & Tips to Increase Your Business’ Cybersecurity
Here’s a handy checklist to run through with your team to ensure you are positioning yourself with the most secure setup possible. While cyberattacks and breaches are going to continue to exist as threats, there are top tips and steps you can take to reduce your vulnerability. Considering the staggering cost and detrimental impact of such an attack, we say it’s best to err on the side of caution and put your safety helmet on.
Two-Factor or Multi-Factor Authentication is worth its weight in gold. This is vital to stay secure by providing a valuable extra layer of security to your system. We recommend Duo, although there’s a whole host of options out there. We can help set this up for you if you’re not already suited n’ booted. If you’re a GloPartner, this is a free and automatic addition to your package.
When using a Two-Factor authentication ensure it is not via SMS. SMS messages are regularly being compromised meaning a potential dent in your security setup.
If an email looks suspicious or out of the ordinary, reach out to the sender via other means to confirm legitimacy. Hey, what’s a short conversation if it saves you hassle in the long run?
A secure password policy is a must. Passwords should be 8-64 characters long, include no hints and should lock the user out after 10 failed attempts. We know it can be time-consuming to conjure up passwords that meet the criteria, but obvious passwords are just an open door to hackers. You can chat with us if you’d like us to provide you with more tips and guidance on a secure password policy.
Anything on your network, especially things connected to the internet, should be patched regularly and on time to maintain the most effective security measures. And don’t forget firmware on your devices.
Invest in Antivirus software. Add another critical layer in your lair of protection.
It is important for businesses to invest and correctly configure a decent firewall. This is often the first line of defense between you and the internet.
Use dedicated admin accounts and stick to them. Admin accounts should only be used by administrators and should not be used for everyday tasks. Tight housekeeping is a great security measure and means if the worst-case scenario does take place, there can be some damage limitation.
Conditional Access Rules can be set up to avoid people accessing your resources with IP addresses that are based outside the UK. This of course applies to UK-based businesses with no employees abroad.
Limit a Bring Your Own Device (BYOD) culture. Whenever possible, employees should work on company devices only. Other devices represent a significant security risk and cannot be securely managed as effectively.
Haveibeenpwned.com allows you to check if your email or phone number has been compromised. Check whether you’ve been previously affected.
Stay up to date on ‘new vulnerabilities’ reports that are released. Let your updates run overnight or leave it to run during your lunch break to reduce your downtime if necessary.
Staff awareness and training are essential to protect against phishing and BEC scams. Invest in training days or short courses to empower your team to think and act securely. We have carried a few of these out for customers to great effect.
If something seems suspicious, report it to us or your dedicated IT team straight away. There is a need for speed. Don’t feel silly bringing up an email you are unsure of, we would rather investigate and reassure you than deal with a much larger issue of a cyberattack.
Cyber Essentials is a Government-backed and industry-supported scheme that helps businesses protect themselves against the growing threat of cyber-attacks and provides a clear statement of the basic controls organisations should have in place to protect themselves. We recommend taking up this scheme for the benefit of your business’ security and installing confidence in your customers. We have taken several of our customers through the process successfully and can help you, as well as provide advice related to your specific setup. Find out more about Cyber Essentials here. (It’s just a badge, but it shows that you have at least thought about this.)
Phew. That was a lot to digest. We understand if you’re feeling pretty overwhelmed right now, but think of it like this: you are more informed and armed with knowledge now than you were before.
If you have any questions, feel free to get in touch and shoot them our way. We would love to help businesses like yours improve their cybersecurity and reduce your risk of an attack. Whether it’s a question or two, you’re in need of team training, or you need us to complete a security assessment to identify where your weaknesses are – we’ve got it covered.